In this blog, we will dive into the process of configuring WSO2 Enterprise Integrator (EI) to work behind a proxy server. We will discuss the necessary configurations and steps needed to ensure that your WSO2 EI can properly connect to the internet and access external resources while being behind a proxy server. Whether you are looking to secure your WSO2 EI or need to comply with organizational policies, this guide will provide the information you need to successfully set up WSO2 EI with a proxy server.
- Download https://squidman.net/squidman/index.html to start a proxy server
- Install and open SquidMan on the server computer.
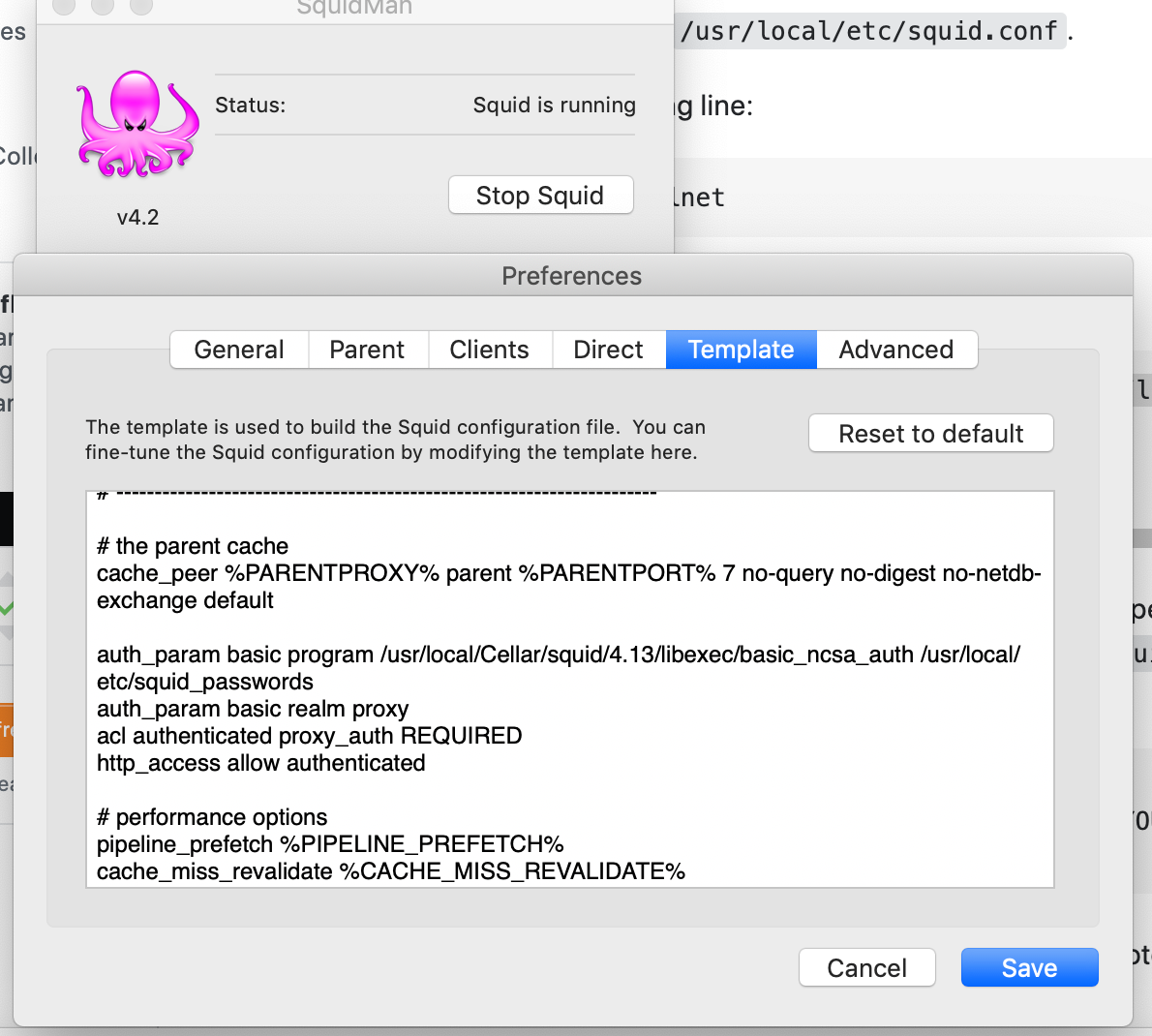
- Optionally, you can use basic authentication to connect this proxy service. For that, create a user and password with following command(I have given admin as the username and admin as the password):
htpasswd -c /usr/local/etc/squid_passwords admin4. (Do this if you follow step 3) Add the following configuration into the squidman template
auth_param basic program /usr/local/Cellar/squid/4.13/libexec/basic_ncsa_auth /usr/local/etc/squid_passwords
auth_param basic realm proxy
acl authenticated proxy_auth REQUIRED
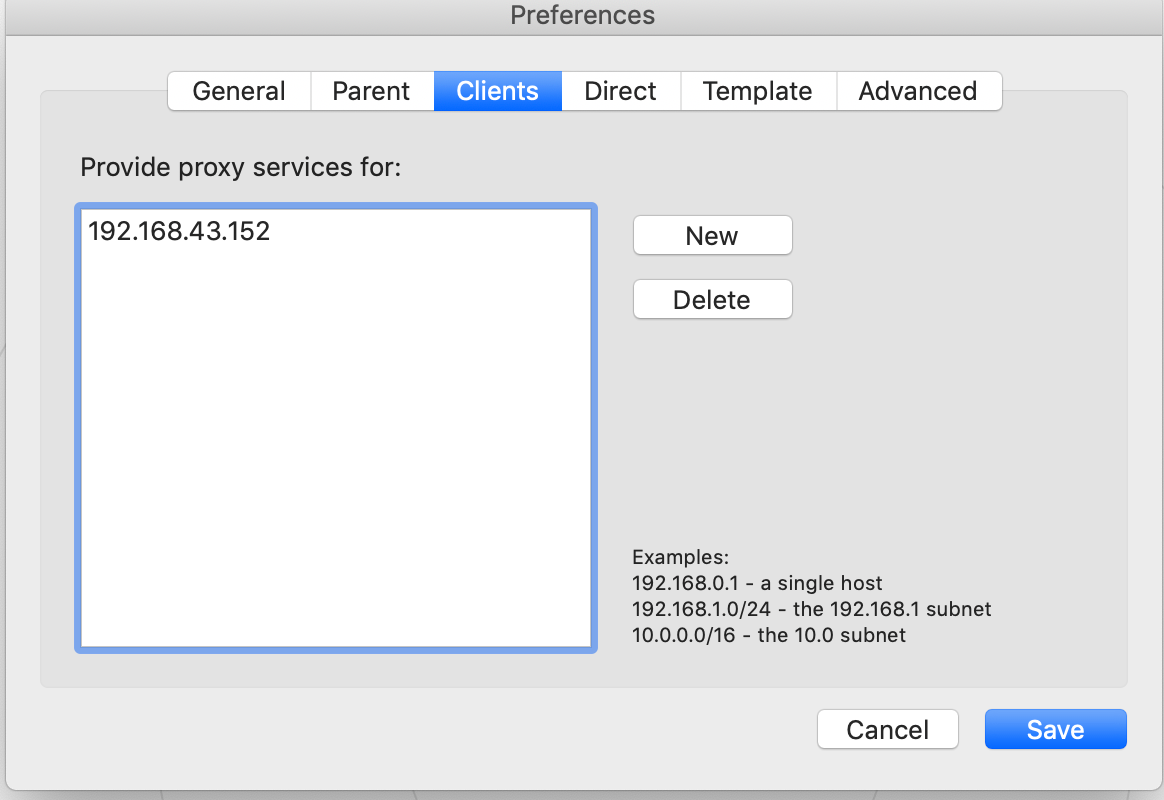
http_access allow authenticated5. Add the client computer IP address that allow to access this proxy with Clients tab.
6. Click Save and start the Squid server.
7. You can now test the proxy server by using following curl command on the client machine.
If you didn’t used basic authentication then:
curl -v -x http://192.168.43.212:8080 http://www.google.com/With the basic authentication, curl would be as follows:
curl -v -x http://admin:admin@192.168.43.212:8080 http://www.google.com/Setting up WSO2 EI/MI
8. Add the following deployment.toml configuration to <MI_HOME>/conf/deployment.toml
[[transport.http.proxy_profile]]
proxy_host = "192.168.43.212"
proxy_port = "8080"
target_hosts = ["*"]
proxy_username = "admin"
proxy_password = "admin"
[[transport.http.secured_proxy_profile]]
target_hosts = ["*"]
proxy_host = "192.168.43.212"
proxy_port = "8080"
proxy_username = "admin"
proxy_password = "admin"If basic auth not defined, then you can ignore proxy_username and proxy_password.
9. Add following proxy service to to MI:
<?xml version="1.0" encoding="UTF-8"?>
<proxy xmlns="http://ws.apache.org/ns/synapse"
name="test"
startOnLoad="true"
statistics="disable"
trace="disable"
transports="http,https">
<target>
<inSequence>
<call>
<endpoint>
<http method="get" uri-template="https://run.mocky.io/v3/7c30406d-3777-4d50-afe2-316f3e0d8a5b"/>
</endpoint>
</call>
<log level="full"/>
<respond/>
</inSequence>
</target>
<description/>
</proxy>10. Invoke the proxy service and you will get the response through the proxy server. If you add invalid credentials for deployment.toml, this will fail.
In conclusion, setting up WSO2 Enterprise Integrator (EI) to work behind a proxy server can be a bit tricky but with the right configurations and steps, it can be done smoothly. By following the guidelines provided in this blog, you should be able to successfully configure your WSO2 EI to work behind a proxy server. It's important to note that different organizations might have different proxy configurations and policies, so it's essential to check with your organization's IT department for the specific configurations needed.
Comments
Post a Comment